Arthur Lynch | Thu Jan 22 2026
Securing Enterprise Access: A Guide to NFC Jewelry Implementation
In the world of enterprise security, the balance between robust protection and user convenience is a constant challenge. Traditional access methods, like plastic keycards and fobs, are often a source of friction—they are easily lost, stolen, or forgotten, creating security gaps and administrative burdens. NFC jewelry for access control presents a sophisticated solution, embedding advanced security into elegant, wearable forms that users are less likely to misplace. These are not mere accessories; they are passive, battery-free credentials that grant secure, frictionless access to buildings, data centers, and corporate events with a simple tap. This guide explores the strategic implementation of NFC wearables, focusing on enterprise needs, security protocols, and management.
The Security Challenge: Moving Beyond Legacy Access Systems

For decades, enterprises have relied on plastic credentials. While functional, these systems are fundamentally flawed. Lost or stolen cards create immediate vulnerabilities, forcing security teams into a reactive cycle of deactivation, re-issuance, and tracking. This process is a drain on administrative resources and introduces unacceptable delays in securing a facility after a credential is compromised. Moreover, the impersonal nature of a plastic card means it is often shared or left unattended, further undermining security protocols.
NFC jewelry addresses these core challenges by fundamentally changing the user's relationship with their credential. An item worn daily, like a ring or bracelet, is inherently more personal and less likely to be misplaced or casually loaned to a colleague. This simple psychological shift significantly strengthens the first line of defense against unauthorized access.
A Modern Approach to Security and Convenience
By embedding a passive, no-battery-needed chip into a durable accessory, organizations can offer a credential that employees and stakeholders want to wear. This approach aligns security with user experience, delivering tangible business benefits.
- Enhanced Security: Wearables are less prone to loss or theft, reducing the risk of compromised credentials and tightening physical security.
- Frictionless Experience: The intuitive tap-and-go action eliminates the need to search for a wallet or bag, streamlining entry and improving daily workflow.
- Improved Corporate Image: Deploying stylish, tech-integrated accessories signals that an organization is forward-thinking and values employee convenience.
- Reduced Administrative Overhead: The significant drop in lost credentials reduces the costs and labor associated with re-issuance and management.
The Growing Market for Wearable Access
This is not a niche concept; it's a rapidly expanding market driven by enterprise demand for smarter security solutions. The NFC smart ring market, a key component in wearable access control, was valued at USD 1.2 billion in 2024 and is projected to reach USD 5.0 billion by 2033.
This exponential growth underscores a clear shift toward technologies that seamlessly integrate security into everyday life. For businesses planning their security infrastructure, this trend is a critical data point. More details on market dynamics can be found in this report from Verified Market Reports. Adopting wearable technology is not merely an upgrade; it is an essential step toward future-proofing enterprise access control.
The Architecture of NFC Access Control
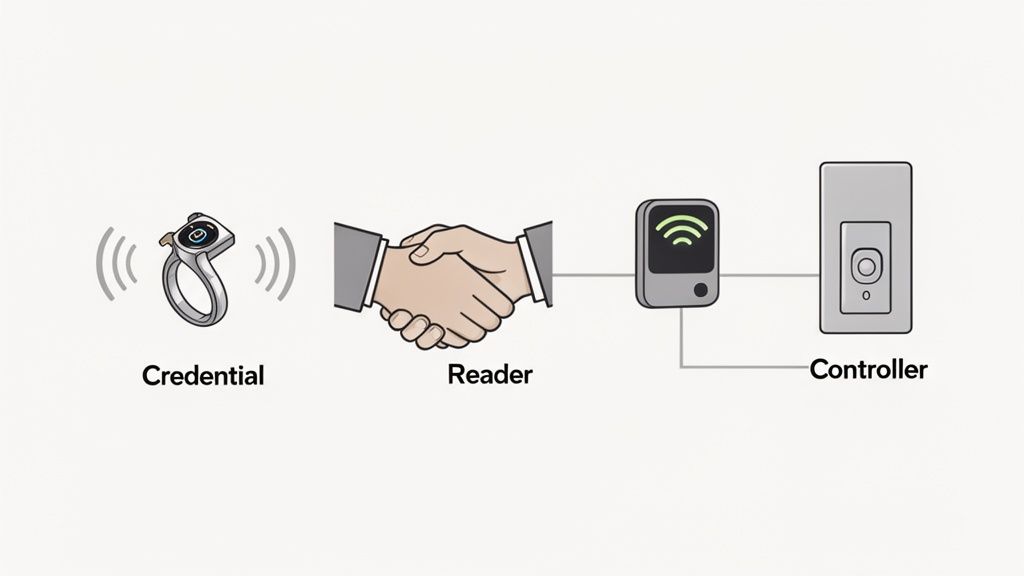
To trust a wearable with enterprise security, it is essential to understand its technical foundation. Near Field Communication (NFC) facilitates a secure, short-range digital handshake between the credential and the access point. When NFC jewelry is brought within approximately 4 centimeters of a reader, the reader's electromagnetic field powers the passive chip inside the jewelry. In that instant, the chip transmits its unique, encrypted identifier to the reader, which then verifies the credentials.
This entire transaction is completed in milliseconds. The "near field" nature of the technology is its greatest security strength; the extremely short communication range makes remote signal interception or "skimming" attacks virtually impossible.
The Three Pillars of NFC Access Control
Every NFC access control system is built on three core components that work in concert to secure an entry point.
-
The Credential (The Jewelry): The ring, bracelet, or other wearable contains a passive NFC chip programmed with a unique identifier. Its battery-free design ensures it is always operational and requires zero maintenance.
-
The Reader (The Gatekeeper): Installed at the access point, the reader continuously emits a low-power radio field. When a credential enters this field, the reader captures its identifier and passes it to the controller for authentication.
-
The Controller (The Brain): This is the central processing unit of the system. The controller compares the identifier received from the reader against a database of authorized users and their specific access permissions. Based on this verification, it instructs the locking mechanism to grant or deny entry.
Key Takeaway: The passive NFC chip is the cornerstone of the system's reliability. With no battery to charge or replace, the wearable credential offers a truly "set it and forget it" solution for both users and administrators.
How Security Is Built-In
The security of an NFC system is multi-layered. Its primary defense is the short communication range, which physically prevents remote data theft. Secondly, the data exchanged during the authentication process is protected by strong encryption protocols. Even if a signal were to be intercepted, the data would be unintelligible to unauthorized parties.
This combination of physical proximity and digital encryption creates a robust security model. While technologically advanced, NFC systems can integrate with and enhance traditional security hardware like magnetic locks for doors. The durability of the wearable itself is also crucial; materials like stainless steel are often chosen for their resilience, an important factor explained in guides on what stainless steel jewelry offers. This fusion of robust technology and practical design makes NFC jewelry an ideal choice for modern enterprise security.
Corporate Applications: Balancing Security and Style
The true value of NFC jewelry is realized in its practical application across various corporate environments. It elevates access control from a purely functional system to a seamless experience that enhances security, efficiency, and brand perception. From corporate headquarters to large-scale events, this technology is solving real-world business challenges.
The benefits are clear and measurable: reduced administrative workload, smoother personnel flow, and a more secure environment that doesn't inconvenience its users.
Securing Corporate Offices and Data Centers
In a corporate setting, managing access is a continuous process. A lost keycard represents an immediate security risk, requiring prompt action to deactivate the old credential and issue a new one. NFC jewelry mitigates this risk at the source. An employee is far less likely to lose a ring they wear daily than a generic plastic card.
This inherent user accountability enhances security posture. For high-security zones such as data centers or executive suites, wearables can be integrated into multi-factor authentication (MFA) protocols. For example, an employee might be required to tap their ring and then enter a PIN code. This two-factor process provides significantly stronger security than a card alone without adding undue friction. The underlying technology must be flawless, a key consideration in the field of security in embedded systems.
Streamlining Large-Scale Events and Hospitality
Event organizers are tasked with managing access for thousands of individuals—attendees, staff, and VIPs—across multiple checkpoints. Traditional tickets and wristbands are prone to forgery and create bottlenecks at entry points.
NFC jewelry, often deployed as a branded bracelet, transforms the event experience.
- Effortless Entry: A simple tap of the wrist significantly reduces wait times and improves attendee satisfaction from the moment they arrive.
- Tiered Access: A single wearable can be programmed with different access levels, allowing VIPs into exclusive lounges while granting staff access to backstage areas.
- Cashless Payments: By linking the wearable to a payment method, organizers can enable seamless transactions for merchandise, food, and beverages, enhancing convenience and increasing sales.
Hotels are adopting similar systems, replacing plastic key cards with stylish NFC wearables. Guests can use a ring or bracelet to unlock their room, access amenities like the spa or gym, and charge expenses to their account, creating a modern, luxurious, and frictionless stay.
Membership Management for Clubs and Facilities
For gyms, co-working spaces, and private clubs, effective member management is paramount. NFC jewelry offers a superior alternative to standard membership cards. A member can use their wearable to check in, access lockers, and pay for services, all without carrying a separate card.
This technology fosters a sense of community and brand loyalty. The wearable acts as a tangible symbol of membership, a valuable perk that reinforces the member's connection to the organization while providing the business with precise data on facility usage.
The Growing Market Powering These Applications
The enterprise adoption of NFC jewelry for access control is supported by a booming market. The broader NFC industry is projected to grow from USD 21.69 billion in 2024 to USD 30.55 billion by 2029. Smart rings are expected to experience the highest growth as users increasingly prefer discreet, fashionable technology.
This growth is fueled by the widespread availability of NFC reader infrastructure and consumer familiarity with tap-to-pay technology. With NFC-based ticketing projected to reach 11.2 billion transactions by 2025, the same technology is perfectly positioned for corporate access. For businesses seeking innovative ways to engage employees or clients, smart accessories are becoming a premier option, as highlighted in guides on corporate event gift ideas.
Comparing NFC Jewelry to Traditional Access Methods
To fully grasp the strategic advantage, it is useful to compare NFC jewelry against established access methods. While each has its place, wearables offer a unique combination of security, convenience, and branding potential.
| Feature | NFC Jewelry | Plastic Keycard / Fob | Mobile App |
|---|---|---|---|
| User Convenience | High (Always worn) | Medium (Must be carried) | Medium (Requires phone) |
| Security Risk (Loss) | Low (Less likely to be lost) | High (Easily lost or forgotten) | Medium (Phone is valuable) |
| Aesthetics & Branding | High (Customizable, stylish) | Low (Generic, functional) | Low (No physical presence) |
| Durability | High (Waterproof, robust) | Medium (Can bend or break) | N/A (Dependent on phone) |
| Upfront Cost | Medium to High | Low | Low (App development needed) |
| Operational Friction | Low (Quick tap, no battery) | Medium (Lost card replacement) | High (Battery, app issues) |
For organizations prioritizing a premium, secure, and frictionless user experience, NFC jewelry provides a compelling solution that extends far beyond simple door access.
An Implementation Guide for Wearable Access Systems
Migrating to an NFC jewelry-based access control system is an evolutionary upgrade, not a complete overhaul. A successful deployment requires a methodical, phased approach that minimizes disruption while maximizing security and user adoption.
This implementation guide provides a clear roadmap for enterprise security managers, enabling a confident and smooth transition to a modern, wearable access solution.
Phase 1: Assess Your Current Infrastructure
The initial step is a thorough audit of your existing access control infrastructure. The primary goal is to determine the compatibility of your current hardware—door readers, elevator panels, and other access points—with NFC technology.
Fortunately, many commercial readers installed in recent years are multi-technology capable and already support the standard frequencies used by NFC credentials. Check the technical specifications of your hardware or consult with your security systems integrator. If certain readers are not compatible, they can typically be replaced with minimal cost and effort, but identifying this requirement early is crucial for accurate project scoping and budgeting.
Phase 2: Source Your NFC Jewelry
With infrastructure compatibility confirmed, the next step is procuring the right wearables. For enterprise applications, sourcing from a B2B wholesale partner is essential. A reliable supplier offers critical advantages over retail channels.
- Material Variety: Choose from enterprise-grade materials like stainless steel or titanium, which offer durability and a professional aesthetic suitable for corporate environments.
- No Minimum Order Quantity (MOQ): This flexibility allows for pilot programs and phased rollouts without requiring a large upfront investment in inventory.
- Customization Options: Reputable wholesalers can brand the jewelry with a company logo, creating a cohesive and professional look for employees.
- Cost Efficiency: Sourcing directly from a manufacturer or wholesale platform provides factory-direct pricing, significantly reducing the per-unit cost and making the overall investment more viable.
This phase is about selecting credentials that meet your technical, brand, and budgetary requirements.
Phase 3: Integrate Your Management Software
While the jewelry serves as the key, the access control management software is the system's brain. This is where credentials are enrolled, access permissions are defined, and access can be revoked. The integration process links the physical wearable to this digital command center.
For most modern access control platforms, enrolling an NFC credential is as straightforward as enrolling a keycard. An administrator scans the new piece of jewelry, linking its unique NFC chip ID to a specific user profile and their assigned access rights.
The system's true power lies in its ability to revoke access instantly. If an employee reports a lost ring, an administrator can immediately deactivate its credentials from the management software, neutralizing the security threat without needing to physically retrieve the item.
Phase 4: Roll Out and Train Your Team
The final phase is deployment. A successful rollout hinges on clear communication and user training. While the 'tap-to-enter' process is intuitive, it is important to ensure all employees understand how the new system works and the protocol for reporting a lost item.
The infographic below illustrates the seamless flow of a unified wearable system, managing everything from general office access to high-security data centers and temporary event credentials.
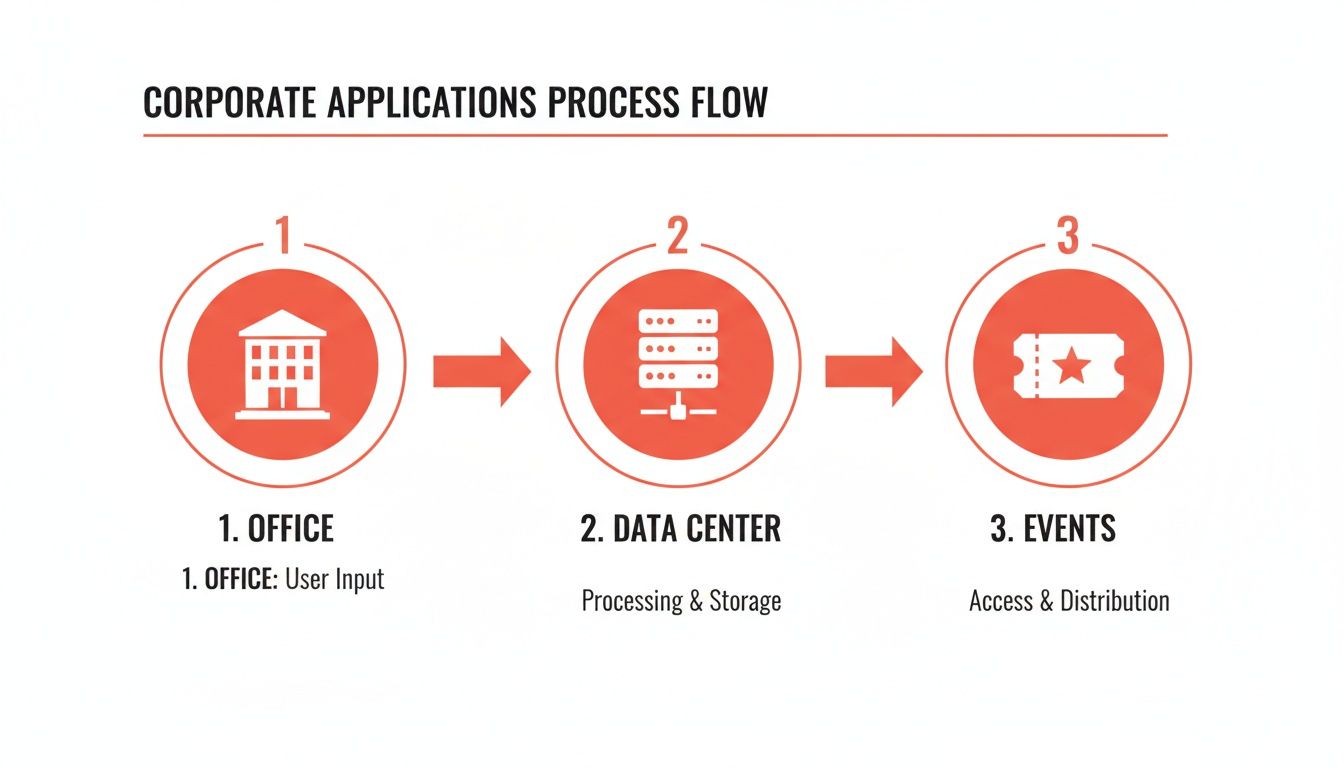
This visual demonstrates how a single credential can be programmed with tiered permissions, simplifying security management across an entire organization. A well-planned communication strategy ensures rapid user adoption, allowing the organization to realize the security and efficiency benefits immediately.
Cost-Benefit Analysis: The Business Case for NFC Jewelry
Ultimately, any enterprise technology investment must be justified by its return on investment (ROI). Adopting an NFC jewelry access control system is a strategic decision with measurable financial benefits. A comprehensive business case weighs the initial investment against long-term gains in operational efficiency, enhanced security, and brand value.
The primary upfront costs include the NFC jewelry itself, potential upgrades to non-compatible readers, and any associated software licensing. By partnering with a wholesale supplier, the per-unit cost of the wearables can be significantly minimized, making the initial outlay more manageable.
Calculating the Return on Investment
The ROI becomes clear when analyzing the long-term benefits. These are not abstract concepts; they are tangible savings and operational advantages that positively impact the bottom line.
The most immediate financial win is the elimination of costs associated with replacing traditional plastic keycards. Businesses continuously spend money to replace lost, stolen, or damaged cards. These recurring costs accumulate into a significant operational expense over time.
A plastic keycard is a disposable utility. An NFC ring or bracelet is a personal accessory that users are inherently more careful with. This shift in user behavior dramatically reduces replacement rates, converting a recurring administrative burden into a predictable, one-time investment.
Hard Savings vs. Soft Savings
The financial benefits can be categorized into two areas. Both are critical to understanding the full value proposition.
-
Hard Savings (Direct Cost Reduction):
- Elimination of Replacement Cards: The budget line item for purchasing new keycards and fobs is virtually eliminated. For a company with 100 employees and a conservative 15% annual replacement rate, this can translate to thousands of dollars in direct savings each year.
- Reduced Logistics Costs: The expenses associated with ordering, printing, and distributing physical cards are also removed.
-
Soft Savings (Operational Efficiency):
- Reduced Administrative Workload: Security, IT, and HR teams spend significantly less time deactivating lost cards, issuing temporary passes, and managing the replacement lifecycle. This frees up valuable man-hours for more strategic initiatives.
- Improved Employee Productivity: Eliminating delays caused by lost or forgotten credentials ensures that employee workflow remains uninterrupted.
Strategic Gains and Brand Enhancement
Beyond cost savings, NFC jewelry delivers strategic advantages that strengthen the organization. A modern, frictionless access experience demonstrates a commitment to employee well-being and convenience, which can be a key differentiator in a competitive talent market.
It also projects a powerful image to clients, partners, and visitors. Adopting stylish, wearable technology showcases the company as innovative, secure, and invested in quality. This aligns with broader market trends; the NFC payment devices market is projected to grow from USD 59.17 billion in 2025 to USD 246.09 billion by 2033, according to Straits Research. As NFC reader infrastructure becomes ubiquitous, the cost for businesses to adopt compatible technologies decreases, making wearables an increasingly astute financial decision.
Viewed holistically, NFC jewelry is not an expense but a strategic investment that delivers returns through lower operational costs, enhanced security, and a strengthened corporate brand.
Management Systems: Sourcing and Supply Chain
The successful deployment of an NFC jewelry for access control program depends on a robust and reliable supply chain. For B2B buyers, system integrators, and resellers, sourcing enterprise-grade wearables is fundamentally different from procuring consumer products. It requires partnering with wholesale suppliers who understand the technical and durability requirements of commercial environments.
The primary objective is to source products that are technologically compatible, durable enough for daily use, aesthetically aligned with corporate branding, and financially viable at scale.
Partnering directly with a wholesale platform or manufacturer is the most effective approach. This provides access to a wider range of materials, customization options, and technical specifications not available in retail markets. A direct sourcing relationship ensures the final product meets the stringent security and durability standards required by enterprise clients.
Key Procurement Considerations
When vetting potential suppliers, several critical factors must be evaluated. The material quality, customization capabilities, and NFC chip specifications are non-negotiable elements that determine the success of the project.
- Material Selection: Since these are everyday-wear items, durability is paramount. Prioritize robust materials like stainless steel and titanium. They offer an ideal combination of strength, a premium feel, and hypoallergenic properties, ensuring they resist scratches and tarnish over long-term use.
- Customization and Branding: The ability to add a company logo or custom engraving transforms the wearable from a generic device into a branded corporate asset. Select a supplier with flexible customization options to create a polished and unified look for your clients.
- NFC Chip Compatibility: This is a critical technical checkpoint. Not all NFC chips are compatible with all reader systems. You must verify that the chip type and frequency within the jewelry are compatible with the client's existing access control infrastructure. Obtain written confirmation from the supplier to prevent costly integration issues.
A crucial but often overlooked detail is the supplier's inventory model. When sourcing factory-direct jewelry, a partner offering no minimum order quantity (MOQ) provides significant strategic flexibility, enabling pilot projects and phased rollouts without requiring a large capital investment.
From Sourcing to Sales Success
Once the supply chain is established, the focus shifts to inventory management and sales strategy. Position these wearables not as mere accessories, but as integral components of a modern security infrastructure.
To resonate with a corporate audience, the sales narrative must center on security, efficiency, and ROI. Frame the product's value around its ability to reduce administrative overhead, eliminate recurring replacement costs, and improve the employee experience.
Building Your B2B Offering
To simplify the procurement process for corporate clients, create bundled packages or "starter kits." This removes the guesswork for organizations new to wearable access control.
A comprehensive starter kit might include:
- An assortment of NFC rings and bracelets in various standard sizes.
- Clear technical documentation on chip specifications for the client's IT department.
- A best-practices guide for employee onboarding and credential distribution.
This solutions-based approach positions you as a strategic partner rather than just a reseller. By providing a complete, well-conceived package, you demonstrate an understanding of enterprise needs and transform a stylish accessory into a high-value business solution.
Case Studies and Common Questions
Transitioning from traditional keycards to NFC jewelry often prompts practical questions about security, implementation, and daily use. Addressing these concerns is key to building confidence and ensuring a successful adoption.
Here, we cover some of the most frequently asked questions from organizations considering this security upgrade.
Is NFC Jewelry Really as Secure as a Standard Keycard?
In many respects, it is more secure. The security of NFC jewelry is based on two core principles: proximity and encryption. The wearable must be within inches of a reader to function, which effectively eliminates the risk of remote signal skimming.
Furthermore, the data transmitted between the wearable and the reader is protected by industry-standard encryption protocols, making it extremely difficult to clone. From a practical standpoint, users are far more likely to notice and report a missing personal item like a ring than a generic keycard, adding an effective, human layer to the security protocol.
What’s the Plan if an Employee Loses Their NFC Ring?
This scenario highlights a key advantage of modern access control systems. If a ring or bracelet is lost, an administrator can immediately log into the management software and deactivate the credential associated with that item. The lost wearable is instantly rendered inert.
A new credential can then be issued to the employee with minimal delay. This process is significantly faster and more secure than legacy procedures like changing physical locks or distributing temporary badges, which can leave facilities vulnerable.
Instant Revocation: The ability to remotely and instantly revoke access for a lost credential is a critical security feature. It neutralizes a potential threat in seconds, closing security gaps far more effectively than traditional methods.
Will This Work With the Security System We Already Have?
In most cases, yes. The majority of modern commercial access control systems are designed for multi-credential compatibility. The critical factor is ensuring the NFC chip inside the jewelry operates on a frequency and protocol compatible with your existing readers.
Many NFC chips use standard protocols widely supported by leading reader manufacturers. The most reliable way to ensure compatibility is to obtain a sample wearable from your supplier and test it directly with your readers before placing a bulk order. This simple validation step can prevent significant integration challenges.
Does This Stuff Need to Be Charged?
No, and this is one of its most significant user-facing benefits. The NFC chip inside a ring or bracelet is a passive device, meaning it has no internal power source or battery.
It draws power wirelessly from the electromagnetic field emitted by the NFC reader when it comes into close proximity. This field provides just enough energy for the chip to transmit its identifier. This battery-free design makes the credential exceptionally reliable and low-maintenance, eliminating user complaints about dead batteries and removing any administrative burden related to charging.
Ready to source high-quality, affordable, and stylish NFC jewelry for your business? Explore the extensive wholesale catalog at JewelryBuyDirect, where you'll find durable options with no minimum order quantity and factory-direct pricing. Start building your modern access control solution today at https://www.jewelrybuydirect.com.
 to show code
to show code












































































































































































